When talking about Bluetooth, we often hear words such as BLE, Beacon, iBeacon, Eddytstone, etc. What are the connections and differences among them? The following is a detailed explanation of the Bluetooth technology involved in common Bluetooth technical terms and applications.
1. Explanation of Bluetooth Technical Terms

Beacon: Beacon is based on Bluetooth low energy proximity sensing by transmitting a universally unique identifier picked up by a compatible app or operating system.


2. The Origin and Classification of BLE
The original specification was developed by Nokia in 2006 under the name Wibree. The company developed a wireless technology adapted from the Bluetooth standard which would provide lower power usage and cost while minimizing its differences from Bluetooth technology. The results were published in 2004 using the name Bluetooth Low End Extension. Wibree is a new radio frequency technology that can work alongside Bluetooth but using just a fraction of the power. The technology was marketed as Bluetooth Smart and integration into version 4.0 of the Core Specification was completed in early 2010.

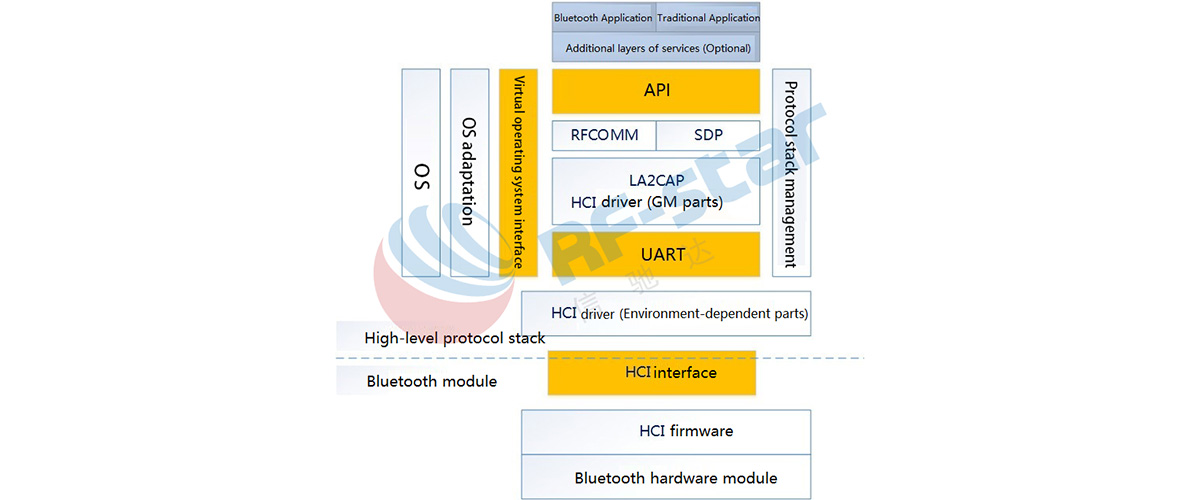
1) Bluetooth devices - Pre-4.0 devices - Bluetooth BR/EDR (Classic Bluetooth).
A Classic Bluetooth device is able to communicate with other Classic Bluetooth devices and Bluetooth Smart Ready devices. Such as wireless telephone connections, wireless headphones, and wireless speakers, etc. SPP (Serial Port Profile) is a Classic Bluetooth profile, SPP defines the requirements for Bluetooth devices necessary for setting up emulated serial cable connections using RFCOMM between two peer devices.
2) Bluetooth Smart devices - Basically Bluetooth low energy devices such as peripherals (think heart monitors, fitness equipment, etc.).
A Bluetooth Smart device can only communicate with Bluetooth Smart and Bluetooth Smart Ready device. It is a protocol that allows for long-term operation of Bluetooth devices in low-volume data transmission. BLE enables smaller form factors, better power optimization, and power cells that last for years on a single charge.
3) Bluetooth Smart Ready devices - Basically devices that could support both Bluetooth low energy and Bluetooth BR/EDR (Classic Bluetooth).
Bluetooth Low Energy technology operates in the same spectrum range (the 2.400–2.4835 GHz ISM band) as classic Bluetooth technology, but uses a different set of channels. Instead of the classic Bluetooth seventy-nine 1-MHz channels, Bluetooth Low Energy has forty 2-MHz channels. BLE is not suitable for communicating large amounts of data, and it is generally used to discover devices and do some simple communications.
Both BLE and Classic Bluetooth can cover up to 100 m range. Compared with Classic Bluetooth, the biggest advantage of BLE is power consumption. The power consumption of BLE is 90% lower than that of Classic Bluetooth, while the transmission distance is increased, and the safety and stability are also improved. BLE supports AES encryption and CRC verification, which guarantees the security of communication between connected devices.
Beacon, as a positioning technology based on the Bluetooth 4.0 protocol, has attracted more and more attention from the indoor positioning market. With the development of the Internet of Things informatization and the continuous accumulation of big data collection and processing requirements, the low-power and low-cost Beacon technology has become the focus of indoor positioning applications. Its characteristics can promote the rapid implementation of the IoT indoor positioning system.
1) No pairing

2) Receive information in the background
The information push of Beacon requires an APP. However, we don’t need to open the APP when we use the indoor positioning function to receive Beacon signals. The corresponding APP only needs to be opened when displaying the Beacon information push service.
3) No data transmission function.
The Beacon device base station only pushes the information needed in the form of broadcast data, and uses the Bluetooth unconnectable mode.
If the APP wants to run and transmit data to communicate with the server to achieve customized functions and obtain specific data, other data communication methods need to be turned on, such as Wi-Fi, 4G, etc.
In addition, Beacon positioning does not need to use the network, which means that the network does not pass through the server. The Beacon positioning algorithm can be implemented locally, and the device itself completes the positioning without calculating through the online server. The premise is that the map data is initialized and written to the local device in advance.
4. The Difference Between iBeacon and Eddystone
1) iBeacon
iBeacon technology is a precise micro-positioning technology based on Bluetooth 4.0 launched by Apple at WWDC in 2013. The underlying technology uses BLE. It is supported after iPhone 4S.
When the smart phone is close to a Beacon, the smart phone can receive the Beacon signal. And the signal receiving range can reach 50 m.

Apple put iBeacon-related interfaces in CoreLocation.framework. Google supports the feature in Android 4.3 and later versions. Developers can use iBeacon technology as long as they meet the iBeacon technical standards. A certain limitation is that the protocol format cannot be modified.
2) Eddystone
Eddystone is a cross-platform open source Bluetooth LE beacon launched by Google on July 15, 2015. It is mainly used to send various information pushes to people in public.
Since Google regards it as an open source project, they does not use the company name to name the open source project. For example, the Android operating system does not use the Google company name. The public does not need to know which company Eddystone is from. Only the OEM who made the beacon and the corresponding app developer know.
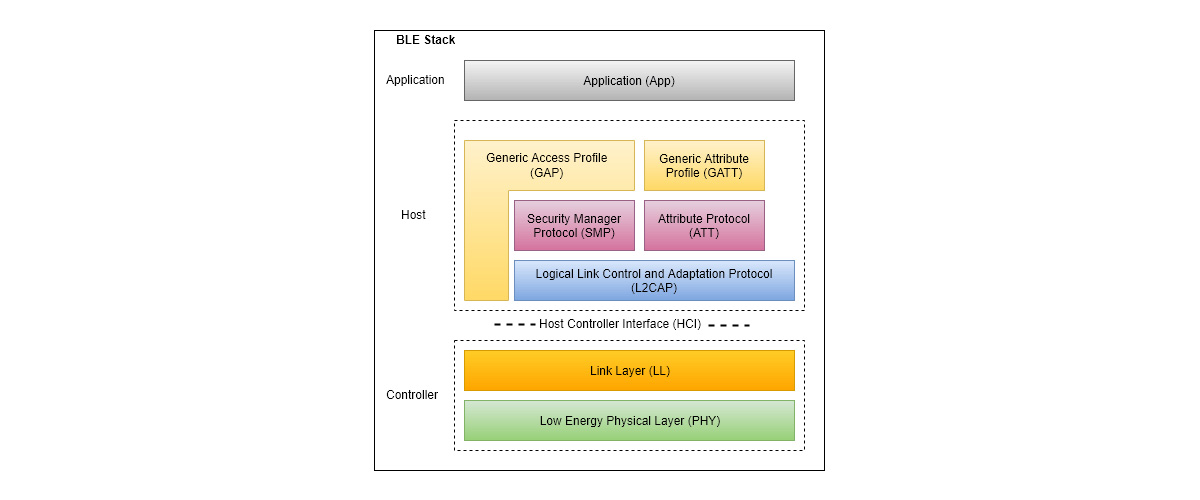
5. How to Use BLE for Beacon Devices
Now, we know what BLE, Beacon, iBeacon, Eddytstone are. Let's take a look at how to implement functions based on BLE technology for beacon devices?
The role of BLE devices changes in peer to peer (i.e. Unicast) or broadcast modes. The common roles are as follows.
Let’s understand how the complete BLE connection work.
1) The process analysis of BLE advertising scan and connection
A peripheral or broadcaster always starts with advertising before accepting a connection. In fact, the advertisement packets are the only way that allows a central or scanner to discover a peripheral or broadcaster. The slave will send a Advertisement Packet every certain time interval. The interval is between 20 ms and 10.24 s, which is called the broadcast interval. The new broadcast internal will affect the connection time for the next boot-up.
The master must receive the broadcast packet before sending the connection request. The slave only monitors the connection request of the master for a period of time after send a broadcast packet. A broadcast packet can carry a certain numbert of bytes of data [BLE4.2: 31 byte; BLE5.0: 251 byte (extended packet)]. It usually contains user name, device information, connectable logo, etc. Broadcast types can be divided into four types:
When the master receives a broadcast packet, it will send a scan request to obtain more broadcast data, and the premise is that the active scanner has been configured. Then the slave responds to the scan request by sending a scan response, which can contain an additional 31 bytes of data.
Broadcast, scan request and response, they use three different 2.4G frequency bands to avoid WLAN interference.
Scanning is used by the master to monitor broadcast packets and send scan requests. There are two timing parameters that need to be noted: "Scan Window" (The length of time for one scan) and "Scan Interval" (The total time of a scan, including the time when the scan is stopped and the time when the scan is in progress). For each scan interval, the master scan time is equal to the "scan window". That is, if the "scan window" is equal to the "scan interval", it means that the master is continuously scanning. Therefore, the duty cycle of the master scan is the "scan window" time divided by the "scan interval" time, and then multiplied by 100%.
When the master wants to enter the connection, it will go through the same process as when scanning broadcast packets. When the connection is initiated and the master receives a broadcast packet, the master will send a connection request to the slave.
The roles of the master and slave are defined according to the first data exchange in the connection. When connecting, the master will request data according to the "Interval" defined by the slave. The interval time is called "connection interval". And it is used for master connection. However, the slave can send connection parameter update requests to the master.
According to the Bluetooth Core Specification, the Interval must be between 7.5 ms and 4 s. If the slave does not respond to the packet from the master within the time-frame, it is called connection supervision timeout, and the connection is considered lost. It is feasible to achieve more data throughput by transmitting multiple packets in each connection interval, and each packet can send up to 20 bytes. However, if the current power consumption needs to be controlled and the slave has no data to send, a certain number of intervals can be ignored. The intervals that are ignored are called "slave latency". In one connection, the device will hop in the frequency band through all channels.
2) How to use Beacon
The Beacon device only uses the broadcast channel, so there is no BLE related connection steps. As the literal meaning of beacon, this device sends data packets at a certain time interval, and the sent data can be obtained by a master device such as a mobile phone.
6. Introduction to the Use of iBeacon Technology
The following mainly introduces how to use iBeacon.
1) Properties of iBeacon
iBeacon is essentially a location information, so Apple integrated the iBeacon function into Core Location. There are three attributes to identify an iBeacon: ProximityUUID, major and minor.
a) ProximityUUID is a NSUUID, used to identify the company. The iBeacon used by each company and organization should have the same proximityUUID, which also known as UUID.
b) Major is used to identify a group of related beacons. For example, in the application of a chain supermarket, the beacon of each branch should have the same major. The role of major is similar to grouping in order to better manage a large number of Beacon devices.
c) Minor is used to distinguish a specific beacon. It is the number management of Beacon devices in the same group. For example, in a chain supermarket, different products on a certain shelf can be distinguished.
If these attributes are not specified, it will be ignored when the device is matched. For example, CLBeaconRegion that only specifies the probabilityUUID can match all beacon devices of a company.
2) iBeacon frame format
The following is the iBeacon broadcast packet frame format. We know that the frame format is composed of parameters such as broadcast length, type, company ID, iBeacon type, iBeacon length, UUID, Major, Minor, and TX power.

The Company ID is to display the company logo. For example, the 16 bit UUID that the following companies apply to Bluetooth SIG: Baidu (0xFDC2, 0xFDC3), Xiaomi (0xFDAB, 0xFDAA, 0xFE95), Alibaba (0xFE3C), Nordic (0xFE59, 0xFE58).
7. Introduction to the Use of Eddystone Technology
The following mainly introduces how to use Eddystone.
1) Properties of Eddystone
Eddystone not only supports open source, but also supports multiple frameworks. Apple iBeacon and Google “The Physical Web” only supported one framework before.
Eddystone is compatible with multiple frameworks, and different beacon vendors sell beacons for different purposes. It means that both iOS and Android phones can receive Google Eddystone Beacon signal. This is a very good news for merchants who need to push store information. It also means that all mobile phones can receive push messages instead of being restricted by the iOS system like iBeacon.
Eddystone multiple frameworks contain data in four formats: UID, URL, TLM, and EID.
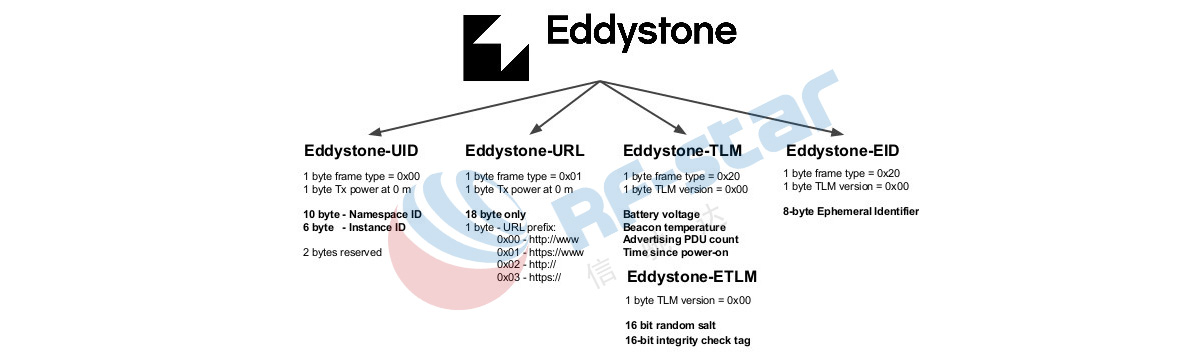
Eddystone's UID was originally intended to be compatible with iBeacon UUID. It breaks the limitation of only iBeacon UUID, UID can be freely set by merchants. The app can choose to only accept messages from this UID. With a unique UID, the merchant app can also determine where the user is in the world and push relevant information, such as coupons, Wi-Fi connections and so on.
URL link is obviously more widely used and simpler than UID. There are browsers on any mobile phone, and they can open the URL. In this one-time transmission, the user does not want to download the app to receive the push information, and the URL is undoubtedly the best choice.
The TLM remote telemetry framework is useful for companies that need to control a large number of beacons. Most beacons are battery-powered, and it needs to be replaced or recharged after a period of time. The telemetry data framework allows the beacon to send its own status like power information to the surrounding staff, so that the staff can be targeted for maintenance and replacement.
EID is a security framework. It is a beacon that only allows authorized users to read information. For example, in a company, beacons are placed in the lobby to broadcast to all customers and visitors. However, the company also has information that it only wants to broadcast to employees. Obviously, they don't want this information to be seen by customers and visitors.
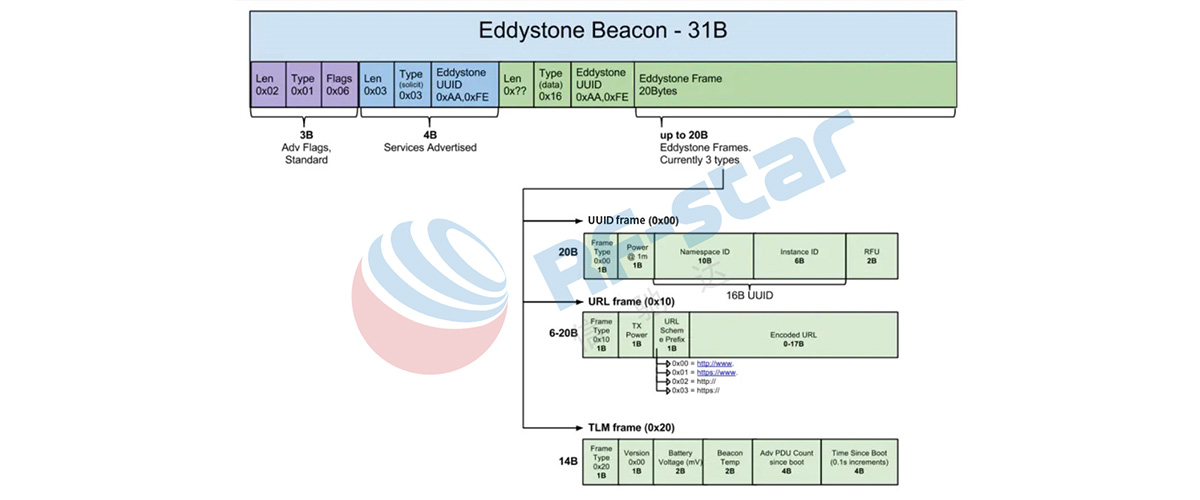
2) Eddystone frame format
Eddystone does not use the manufacturer data field, but puts the 0xFEAA value in the complete 16-bit service UUID field, and uses the associated service data field to contain the Beacon information. Here are the full details.